In today’s world, technology is the backbone of virtually every organization. Reliable and efficient systems are essential for the organization to meet its goals.
Creating a technology audit template provides a framework for conducting a successful and influential company audit. It also serves as a guideline for evaluating IT systems and ensuring their operational, security, and compliance standards.
The technology audit evaluates the physical IT infrastructure and includes policies and protocols that must be followed to ensure a safe and secure system’s operation.
This article discusses the critical components of a technology audit checklist, how to create one for your organization, and best practices.
Why is Technology Audit Important?
Technology audits are detailed evaluations of an organization’s Technology infrastructure, including hardware, software, networks, and data management systems. They ensure the smooth running of the Technology infrastructure.
It helps in risk management by identifying potential threats to the system, such as system breakdowns, cyberattacks, and data breaches. It also improves the system’s efficiency by identifying areas for improvement and providing valuable recommendations. This approach also helps improve efficiency and cost savings by identifying inefficiencies in the system.
Regular technology audits also help a business gain the trust of stakeholders through best practices and certifications designed for technology safety.
Also Read: How Much Does Technical Due Diligence Cost?
Why Do You Need a Technology Audit Checklist?
A technology audit checklist is a detailed document that helps you evaluate your company’s technology infrastructure and performance. It is documented proof of how the audit is conducted and the process’s outcomes. The checklist also includes the weaknesses and points of improvement in the current system.
Critical Components of an Effective Technology Audit Checklist
A technology audit checklist looks into the following components of technology:
Hardware Assessment
Hardware assessment involves auditing physical systems. This includes the hardware, its functionality, and physical security checkups, such as server room security, entry and exit parameters, etc.
Software Evaluation
It involves the use of proper software tools. Are they in a timely manner? Is any unlicensed or potentially dangerous software being used? It also checks the compatibility of the existing software with the systems used in the organization.
Network Security
A network security audit evaluates software such as firewalls, VPNs, or other protocols. The protocols to be followed after a cyber-attack are also reviewed.
Data Management
Data is, in fact, an organization’s most valuable asset. In a data management audit, the data backup processes and protocols, such as the frequency of data backups and the availability of an offsite data backup storage protocol, are reviewed.
It also analyzes the company’s data access protocols, such as the data access levels, data availability to different users, and data access protocols to third-party apps and software. It also looks into the data security procedures so that essential data cannot be leaked.
User Access Control
Every organization has a management hierarchy, and each person has specific roles. Similarly, each user needs data related to its domain. So, providing only the relevant data to a specific user is essential.
Access control is significant for this purpose, and periodic data access evaluation ensures data safety.
The User Access control audit evaluates the data authorization pyramid, role management, and policies.
Compliance Standards
Each business has its specific requirements for technology audit. For example, hospitals and medical facilities have patient data. They also have specific health protocols to follow. Similarly, financial institutions such as banks have financial transactions.
So, along with international best practices, they have other vital protocols that should be included in the technology audit checklist.
Also Read: Technical Due Diligence Process 2025
Technology Audit Checklist Template
Depending on your auditing system, the following attributes should be used to create a technology audit checklist. Along with these, the organization’s specific requirements should also be considered.
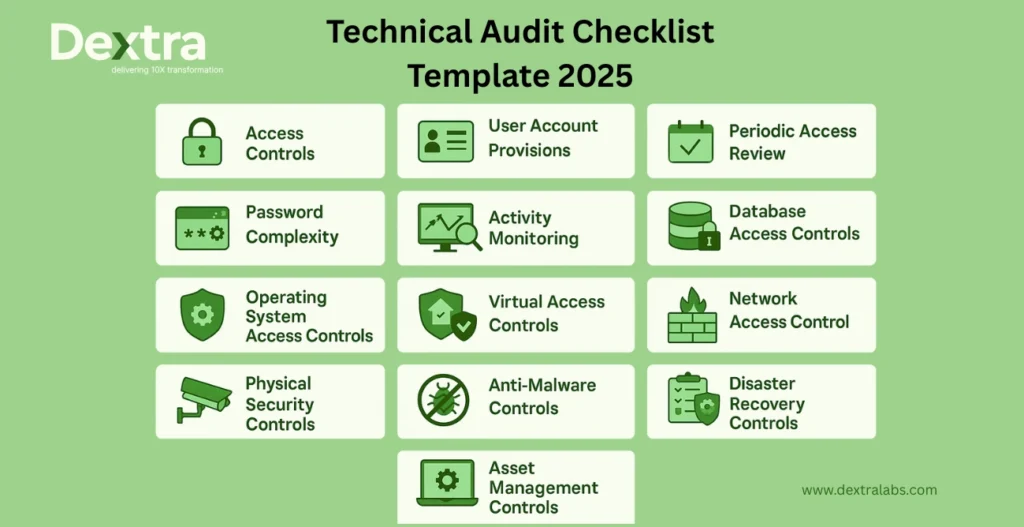
Access Controls
User Account Provisions
The user identity management system allows a user to access the system. It includes user data such as name, employee code, username, password, and the level of data access to a specific user.
Periodic access review schedule
An access review protocol should be in place, and a user’s access should be reviewed periodically to ensure data security.
Password Complexity requirements
Password complexity requirement ensures the security of a password. The users should create passwords of a standard length and data type, for example, the use of alphanumeric characters along with special characters. The password should also be renewed after a specific period.
Activity Monitoring
User activity monitoring tools should be used to ensure the secure use of user accounts. Any irregular activity should be traced and evaluated regularly.
Database Access Controls
Database admin accounts are controlled
Access to a company database should be restricted to certain levels, and a control system should be appropriately implemented to avoid data leaks and breaches. The database access should also be monitored regularly.
Application access to the database is restricted
Third-party applications’ access to company data should be restricted to the required data.
Operating System Access Controls
A system installation checklist document should be prepared and used whenever necessary for troubleshooting and new installations. Ensure the system uses security and event logs to prevent unauthorized access. Turn off all unnecessary services in the operating system, keeping the system safe from malware attacks.
Virtual Access Controls
A Virtual Machine Monitoring system (VMM) should be used with restricted access to enable security from unauthorized system access. Users should have access levels on virtual machines to enable system security and prevent data breaches.
The access review protocol should be in place to periodically review the access levels. Password complexity requirements for virtual machine access should be used.
Network Access Control
A firewall’s availability and proper function should be assessed for remote access to avoid unauthorised access. IDS, IPS, VPN, MFA, and other security systems for remote access should also be inspected.
Physical Security Controls
Physical systems such as Locks, security alarms, HVAC, Backup Generators, Badge Access, and Emergency protocols should be checked during the technology audit.
Anti-Malware Controls
The technology audit checklist should also include inspecting anti-malware controls, including Anti-Virus software, Gateway filtering tools, and Browser protections such as VPNs.
Data Protection Controls
The data protection protocols should be analyzed, including data encryption during transfer and storage, data classification, restrictions on external devices such as USB, and data removal from other temporary storage spaces.
Disaster Recovery Controls
A detailed disaster management and recovery protocol should be in place, and its effectiveness should be analyzed during the audit. The protocol should include system and data backups and a data recovery plan. The business’s data loss and recovery costs should also be analyzed.
Asset Management Controls
The Technology audit checklist should also include hardware and software inventory audits. Check for unauthorized software installations, system capacities, and performance monitoring.
Technology Audit Best Practices
ISO/IEC 27001: Security management
The ISO/IEC27001 standard guides organizations in implementing tech security systems. If an organization is certified for ISO/IEC27001, it has a reliable system to safeguard its data.
It reduces the risk of cyberattacks, ensures paper-based, digital, and cloud-based data security, provides a framework to secure data in one place, and prepares the organization for upcoming security threats.
COBIT: Comprehensive IT audit procedure
COBIT is a comprehensive framework that helps govern IT services and align them with their business goals. It was developed by the Information System Audit and Control Association (ISACA).
When implemented correctly, it enhances system security, aligns information technology with business goals, helps them comply with regulatory requirements, enhances risk management, and boosts operational efficiency.
ITIL: IT service management
It is a framework that involves streamlining IT services to cater to an organisation’s and its customers’ needs. Each organisation can adopt a relatively flexible framework according to its current rules and requirements.
The main aim of ITIL is to enable IT services to provide maximum efficiency and effectiveness to the organization. It standardizes the current IT processes, improves customer experience, enhances service quality, increases system flexibility and agility, and covers the overall lifecycle of the IT system.
PCI DSS: Payment Card Industry Data Security Standard
It is an internationally recognized set of standards to protect credit card transactions globally. It applies to all credit card transaction organizations, including payment processors, merchants, and financial institutions.
The framework provides detailed guidelines to secure sensitive payment data, including storage, processing, and transmission. It prevents data breaches, reduces fraud, and protects consumers’ sensitive information, such as credit card numbers and personal details. Organizations that comply with PCI DSS can establish trust with their customers while reducing legal and financial risks.
How to Create a Technology Audit Template?
Technology audits can differ from business to business depending on their requirements and standard protocols. The following steps should be followed to create a technology audit template for your organization.
Define Audit Scope
While creating a technology audit template, the audit scope should be identified. The scope should be aligned with the organization’s objective.
It includes defining the audit’s objective, specifying the assets for which the audit is being conducted, and determining the stakeholders impacted by the audit, such as IT teams, company management, and any external partners. It is also essential to set the time frame for the audit to ensure minimum disruptions during the audit.
Risk Assessment
Risk assessment should identify potential risks to IT assets, such as data breaches, hardware failures, or outdated software. It should also assess each risk’s potential impact on business operations, finances, and reputation.
Risk assessment helps to identify and prioritize the high-risk areas for the audit. It also prepares for any interruptions that can occur during the process.
Audit Team
Create a team of competent professionals with in-depth knowledge of the systems and processes being audited. The success of an audit relies on the team you will work with.
Audit Plan
Create a detailed roadmap to guide the audit process. It includes audit areas, roles and responsibilities, potential threats and disruptions during the audit, timelines, audit outcomes in audit reports, and methodologies to follow during the audit.
Wrapping Note
A technology audit template is fundamental for an organization to conduct a successful company audit. An efficient IT system is crucial for an organization’s success, and a technology audit ensures that the system is working at its full potential, providing a safe and secure working environment in terms of data security, minimum breakdowns, and safety from cyberattacks and data breaches.
A comprehensive IT audit template helps in a seamless technology audit that covers the whole system, including hardware, software, and data safety. Hence, creating and using an effective audit template is vital to a successful audit.
FAQs on It Audit checklist template:
Q. Why is a Technology audit checklist essential?
A Technology audit template is essential to make sure all critical parts of IT systems are analyzed, risks are identified, and the organization follows rules and best practices.
Q. Why is an audit checklist important for small businesses?
IT audit checklist is vital for every business, regardless of its size. It ensures safety and efficiency and increases the performance of your existing system by providing valuable information about weaknesses and areas for improvement.
Q. What is the purpose of a technology audit?
A technology audit analyzes the whole IT infrastructure. It provides an in-depth report of current weaknesses and areas for improvement, aligning with your organization’s goals and improving the system’s overall efficiency and effectiveness.